How to create an identity verification process
Here at Veriff, our online identity verification solution provides a thorough verification process and handles compliance on your behalf. By leaving identity verification to us, you can focus on doing what you do best.

Raul Liive
Veriff’s online identity verification solution provides a thorough biometric identity verification process on your behalf. We are the knowledge-holders for everything related to the personal documents required for verification and, by leaving identity verification to us, you can focus on doing what you do best.
We know that anti-money laundering (AML) and know-your-customer (KYC) requirements are unique for each business. As a result, it's vital that you have an identity verification process that suits your specific needs and requirements.
To help, we've created this guide, which outlines how our identity verification platform works and the things you should consider when building your own identity verification process.
1. What is identity verification and how does it work?
Identity verification plays a vital role in confirming individuals' identities, particularly in online interactions. It involves validating personal details through steps such as examining ID documents and biometric data. Digital identity verification processes using specialized software are crucial for online security and trust. Various methods, such as knowledge-based verification, are used to prevent fraud and enhance security measures. Understanding these processes is essential for businesses to choose the right verification methods.
- Verifying a user’s identity involves various approaches to confirm authenticity. Common methods include:
- Document Verification: making sure that document is real
- Biometric Verification: using fingerprints, facial recognition, voice, or iris scans to carry out a liveness check
- Knowledge-Based Verification: asking personal questions.
- Two-Factor Authentication (2FA): using a password plus a code.
- Social Media Verification: confirming identity using social profiles.
- Video Verification: confirming identity visually.
2. What information needs to be verified?
Generally speaking, the identity verification process ensures two things. It checks that the person who is attempting to sign in to access your services is a real person – and not a bot or an AI-generated ‘person’. Second, it confirms that the person who is attempting to access your services is exactly who they say they are, that they have a real document and that the document is theirs and is valid.
By verifying the genuine identity of a user, you can prevent any identity theft or fraud. You can also prevent someone with a false identity or stolen identity from accessing your services.
In the online world, there are different approaches to digital identity verification. Of course, unlike in a shop, there's no physical interaction between the service provider and the client. But, by using an online remote identity verification services solution like ours, you can verify users in seconds.
Our solution verifies that:
- An ID is real and has not been tampered with
- The information on the ID matches the individual in question
- The person uploading the ID is also the person on the ID
- The session or user is ‘live' and the user is real
- A user is not prohibited from using your services because they've been sanctioned
- The user is of a valid age
- The user is in the appropriate country
3. Using an identity verification platform
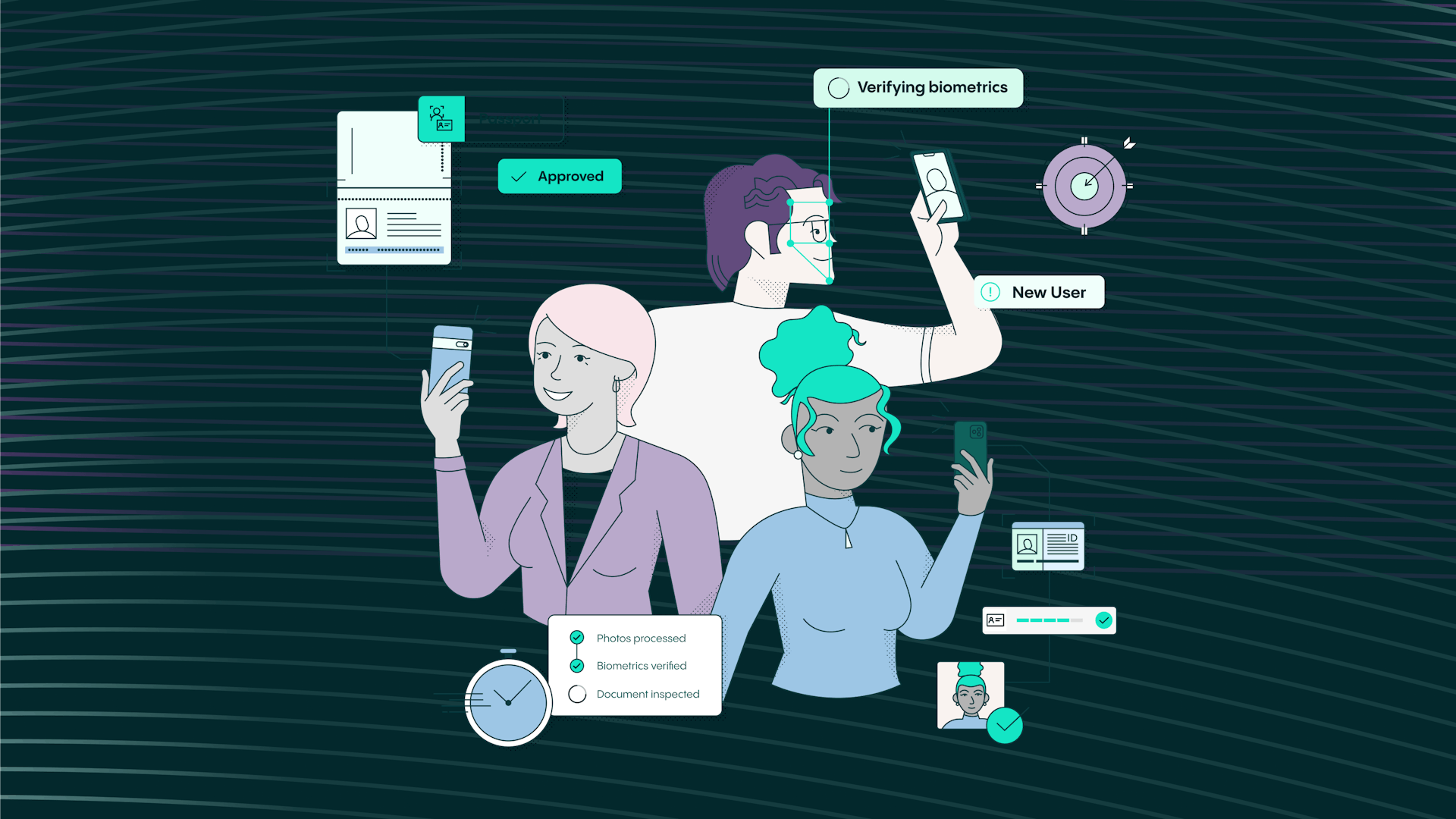
Our online identity verification solution provides a thorough verification process and handles compliance on your behalf – through an end-to-end verification service. This is accomplished in three simple steps:
Verification flow
User biometric data is gathered for analysis during the verification sessions. The personal information gathered from the user will depend on the document they provide for verification (usually a passport, ID card or driving license).
Although our identity verification solution makes this part of the process look simple, a lot of work is carried out behind the scenes to make sure that verifications are accurate and don't negatively impact your conversion rates. This background work includes browser and device analytics, optional background video checks, and other data cross-checking methods.
To help you even further, we:
- Support over 12,000 identity documents from across 230+ countries and territories
- Analyze your traffic for any fraud patterns or suspicious activity and block the bad actors
- Automatically collect the category of driver's license as an additional data point, if required
- Help you customize web and mobile flows so they align with your branding
- Can add or remove steps for your users
- Include the option for background video recording, which allows us to conduct advanced fraud prevention checks
- Use AI technology to assess client sessions in real-time and guide users during photo-taking steps
Verification engine
During this stage, the verified data set that was collected from the customer is analyzed. We understand that a one-size-fits-all solution does not work for verification. For example, some use cases are really sensitive to fraud, while some are more focused on getting as many good customers through as possible. That’s why we provide a number of optional features to scale fraud prevention up or down.
Our verification check engine can be configured to enable the checks you need. Options include:
- Network and device analytics
- Automated data extraction
- Document validity checks
- Biometric analysis
- Liveness checks
- PEP and sanctions checks
- Registry checks
- Age validation checks
- Velocity checks
Verification platform
Once a customer has started the verification process, live session statuses and results can be viewed in your Veriff Station. You can manage multiple integrations and automate the flow of information with webhooks. And you can restrict data permissions to keep your user data secure.
4. Tips for getting it right – and benefiting your business
Keep your business compliant
For regulated businesses, such as those in the healthcare, banking, and pharmaceutical industries, KYC compliance is an important part of establishing trust with customers.
While KYC compliance is a requirement in regulated industries, knowing your customer should be the best practice for any growing business that wants to transact and interact with trust and confidence.
Keep the process short
Generally speaking, the longer the conversion process, the more customers will drop out of the flow. Therefore, the identity verification process you create should be as short as possible and contain only a few steps.
After directing your customers to your flow, you should ask them to take either one or two photos of the ID they've selected. At this stage of the customer experience, you should be clear about the photos you need from them, the quality of the photos you require, and the information on the ID document that needs to be visible. If necessary, you can also ask them to input some basic data and then scan and verify their identity document. This process works well for biometric passports.
Finally, ask them to snap a selfie and confirm everything is fine. Once everything is confirmed, your identity verification platform can complete the verification and send the customer back to you.
Drive conversion rates
When building your own verification process, you need to keep an eye on conversion rates.
Although the best practice for converting customers is to shorten the conversion funnel (as mentioned above), regulatory requirements such as KYC compliance laws or the European PSD2 directive may require extra steps in financial processes to be added to the process.
Due to this, you need to be smart about the way you guide your users through verification. By pushing certain steps to the background, you can reduce the amount of work your customer has to do while still meeting compliance laws.
Build trust wherever you can
Users want to know that their information is safe and their government agencies' identity documents secure. This is understandable because they're providing you with photos of their government-issued identity document.
As a result, reassuring your user goes well beyond writing supportive copy. To encourage as many users as possible to go through the verification process, you should also create visual clues that will establish trust, authenticity and authority. These can include GDPR badges and videos that show your employees going through the steps.
Other subtle ways to establish customer trust can include maintaining your visual brand throughout the process. To help with this, we offer SDK customization options that can help stop customers from feeling like they're being redirected to a third-party site.
Provide user guidance
Finally, once you've created your own identity verification process, you should actively help guide your customers through it. By providing useful documents and helpful tips to your customers, you'll boost your conversions and make the identity verification process work straightforward.
Learn more
Get the latest from Veriff. Subscribe to our newsletter.
Veriff will only use the information you provide to share blog updates.
You can unsubscribe at any time. Read our privacy terms



